Cybersecurity Threats for Legal Confidential Documents
In the case of a matter of spell to handle legal papers, cybersecurity is not the pinnacle significance; it's genuinely crucial. These organizations treat one of their most valuable assets with due care by making these confidential records safe, resulting in increased customer trust and the organization being in line with data protection laws. Through the implementation of identity authentication, encryption, and cybercrime threat defense, [legal documents are protected from unauthorized access and safety threats.](https://brightreturn.com/document-management-landing/).
Privacy is one of the cornerstones of BrightReturn services as it projects its documents as vital and supports safety measures to prevent theft and manipulation. They accomplish this by implementing total security systems, giving security to information, and shielding lawyers from the danger of misuse or information theft while still keeping accessibility and information integrity.
Significance of Cybersecurity in Legal Document Management
The case of cyber safety in legal document management must be noticed because it is a must-duty for both to keep the attention and discharge the role. The vast amounts of data that transit law firms' communication channels, where several types of legal documents and client contracts are present, give attackers numerous ways to make confidential and vital information become public, which, therefore, carries high costs. Breaching cases hurt trust, fundamentally change reputation, and jeopardize the attorney-client relationship that has existed for decades. Breaching cases smear the white of the attorney-client relationship and ruin the attorney's reputation.
The authorities inspect and check the data security and later give out serious penalties for such breaches, which highlights the serious need to follow stringent regulations like HIPAA and GDPR's rules. Law firms are expected to elevate their defenses against sophisticated adversaries, so their cyber security threat management is unlocked with the encryption password, multifactor authentication, and training employees with security initiatives. Protecting cybersecurity is not only a matter of legal requirements; it is a matter of putting the trust and respect of the client, the professional image, and the company's reputation. In this view, BrightReturn becomes a pillar of security, the element ready to guide a business through legal entities' digital transformation by water storms.
Ideal Aspects of the Legal Documents' Protection Strategies
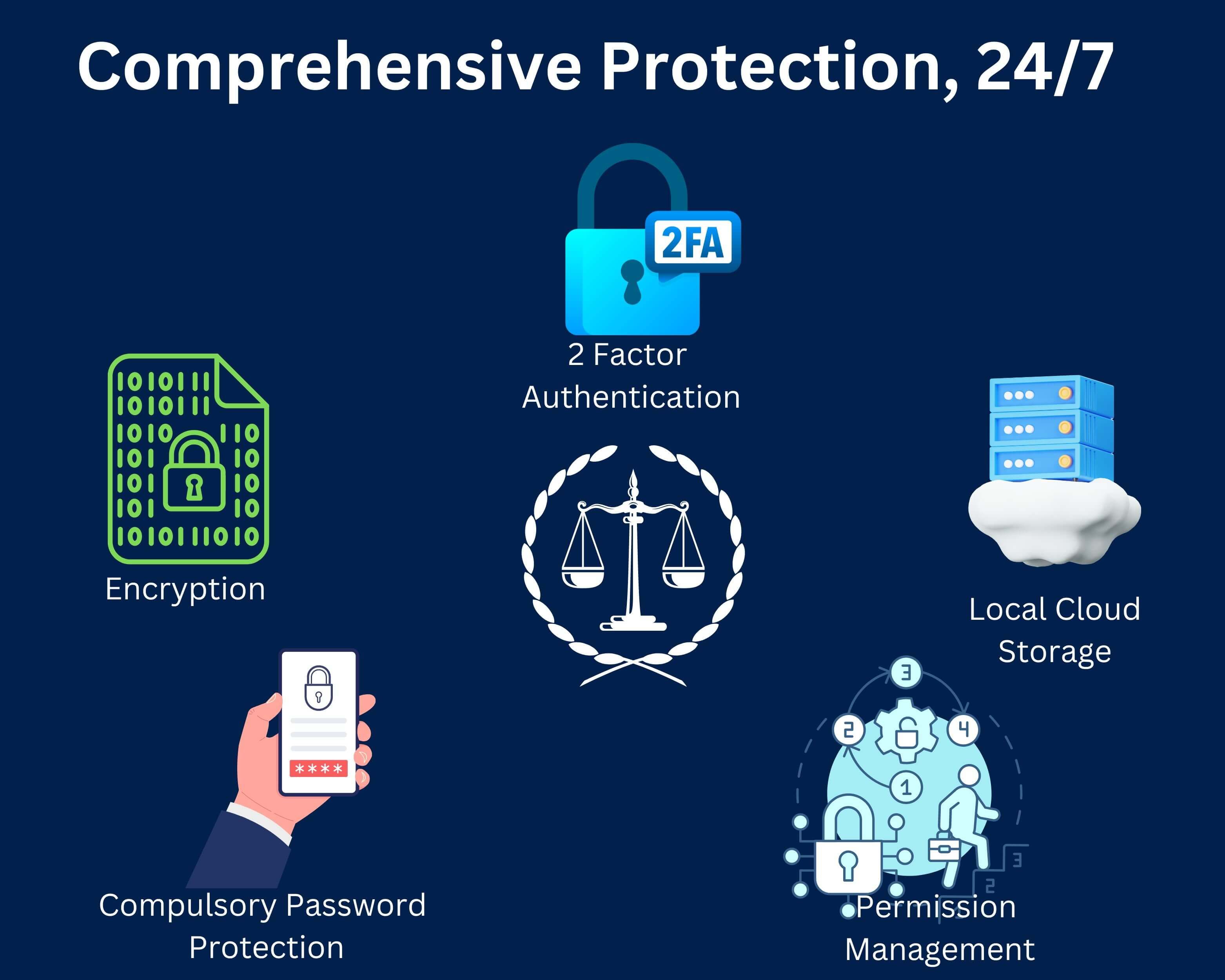
From the standpoint of legal documents, standard security is a must and should be used as a reference rule. Encryption constitutes the primary mechanism that permits keeping information of secondary meaning in the state when it still does not understand anyone unauthorized, even if a copy is intercepted. Instead of encrypting documents across transit and rest, law firms can avoid data breaches and thereby ensure the confidentiality of the client's data with BrightReturn.
BrightReturn maintains thorough security guidelines to defend delicate information, utilizing a far-reaching exhibit of measures:
User Authentication
User authentication is a significant security standard restricting access to credited users' particular data. It is the primary defense mechanism that checks the access request from unidentified users and requires the entrance users to provide proof of their identity. These precautions consist of passwords, biometrics, and two-factor authentication that serve as barriers that put offenders on the defensive and ensure the security and privacy of sensitive information.
2 Way Authentication
The two-step protocol, or two-factor authentication (2FA), offers extra checkpoints for accounts by requiring an additional authentication step. A username and password are the first layer of security. Then, you have an option for an authentication code that is either sent through SMS or biometric data from mobile devices.
Auto Signou
An auto signout strategy improves cybersecurity because the users will be logged out within a specified period of inactivity. Thus, the risk of unauthorized access is reduced. This is a vital marker when users share the same devices and can't dispute. It also inhibits hijack sessions of attackers.
Mandatory Password Changes
The imposition of password changes every three months is instrumental in increasing data security for personal accounts, banks, and other organizations that contain sensitive client information. Frequent alerts get rid of unauthorized access or data breaches, while hackers mainly exploit unwelcome passwords. Reinforcing policies that require password updating regularly keeps organizations on the edge of advances in security relating to a threat and certainly reduces the susceptibility to compromise of the credentials.
Data Encryption
The encryption of information put away on the Amazon Web Administrations (AWS) S3 server is one of the essential components of network safety, and it assumes the most necessary part in safeguarding defenseless data. By utilizing Amazon S3 data encryption, the level of security on stored data is enhanced further than the basic one because even if unauthorized members reach the data, it remains unreadable without the encryption key.
Strict Permission Management
The correct permission management, implying that permission management can control access to sensitive data and resources, is the most critical part of cybersecurity. The implementation of these protocols helps businesses to make sure that personal data is accessible only by people who are allowed to access such data, resulting in a decrease in security incidents.
Secure Client Portal
The Client Portal is the backbone of cybersecurity, providing a convenient and secure channel for businesses to share their files with clients. Effective handling of the growing cyber-risks means the protection of confidential information is of crucial importance. Providing a secure client portal removes the weak file-sharing link, which successfully prevents security hacks.
Role of Advanced Security Features
Enhanced Data Protection
Implementing powerful security features, such as cryptographic encryption and multifactor verification technology, are the top-level defenses of client information. Meanwhile, they nullify or reduce the risk of unauthorized access.
Improved Compliance
Highly secure practice management software allows law firms to hold regulations and data protection laws by putting various access controls and audit trails in place.
lient Trust and Credibility
By utilizing more state-of-the-art security features, law firms reinforce the idea of protecting their client's information, which, in turn, builds the level of trust and credibility among the client base.
Peace of Mind
Computer security applications offer solace to lawyers and their clients as these assurances provide strong assurance against potential cyberattacks and unauthorized access to delicate personal information.
Cost Savings
Through all the proactive implementation of the security measures in managed software practice, we actually decrease the risk for companies of both fines and legal penalties due to data breaches or non-compliance.
Advanced data safeguard systems from BrightReturn in practice management software are required to improve data protection and compliance and build trust and credibility between clients and organizations. The software provides a secure environment for law firms, among other things, in the issues relating to sensitive information, the reduction of security risks, and the confidentiality and integrity of their clients' data.
Reporting of Cybercrime
In the last few years, a growing concern has been seen in defending against cybercrime by utilizing modern document management systems, which can be evident in the data breach reduction instance of the organizations where such systems had already been implemented. There are increasing groups of providers for this type of protection, and the products have features of encryption, access control, audit trails, and data masking used to hide information from unauthorized entities. The possession of these systems' capacity to fast-track detected security gaps is equally important, as it entails vigilant watch and information treating the security gaps.
The statistics speak volumes: business entities adopting or applying to their document management are specially targeted at mitigating the consequences of a data breach, thus becoming more read-only and enhancing the organization's cybersecurity posture and regulatory process. American and Canadian lawyers need to adapt to the present-day realities that incorporate strict data privacy regulations and the all-time risks of cyber hacking. With the mighty all-in-one treasure trove of tools from BrightReturn, specifically cloud services that boast top-notch security, including client portals access control and audit trails, firms will find it easier to shield clients' trust, reduce risk, and maintain a stainless reputation in a digital era that is continuously evolving.
Bottom Line
Through BrightReturn, by applying encryption, access controls, and perpetual cybersecurity education, law firms will be able to protect their security and generate proactive security awareness. Organizations should bear the burden of secure data, and they can do this through persistent focus on data security and proactive steps. Thus, the firms will be able to live up to their professional obligations to the clients and stand out among their competitors as leaders in data protection in the digital age.
Practice Management Software For Revolutionizing Firms
Secure File Sharing Portal with Bright Return
Secure file sharing portals have become a mainstay of business operations in virtually every sector for some time now. From working with confidential client data, to sharing files while collaborating on projects across your remote team members and ensuring that everything you do is compliant with regulations or privacy laws, it is essential to have a safe foundation for file exchange.
